IT Security And Compliance
- Windows Registry
- Drivers
- Installed software
- Security Policies
- Services
- Network Share Files
- Network Share configuration
- Local Users / Groups
- Active Directory / LDAP
- Microsoft Exchange
- Network Devices – Firewalls, Switches, Routers
- Hypervisors – ESXi, HyperV, XenServer
- Databases -MSSQL, Oracle, MSQL, Maria DB, IBM DB2
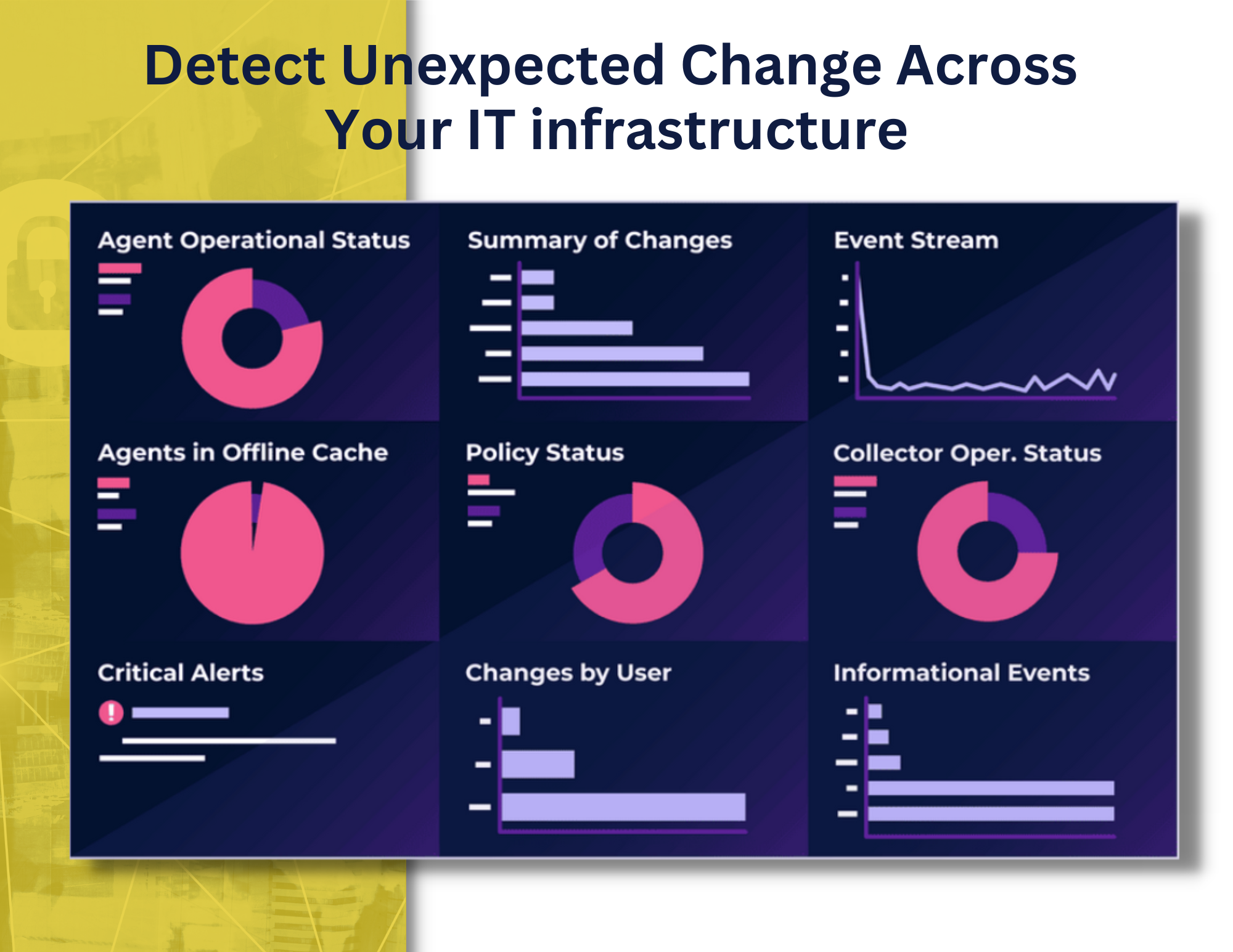
Why File Integrity Monitoring (FIM)
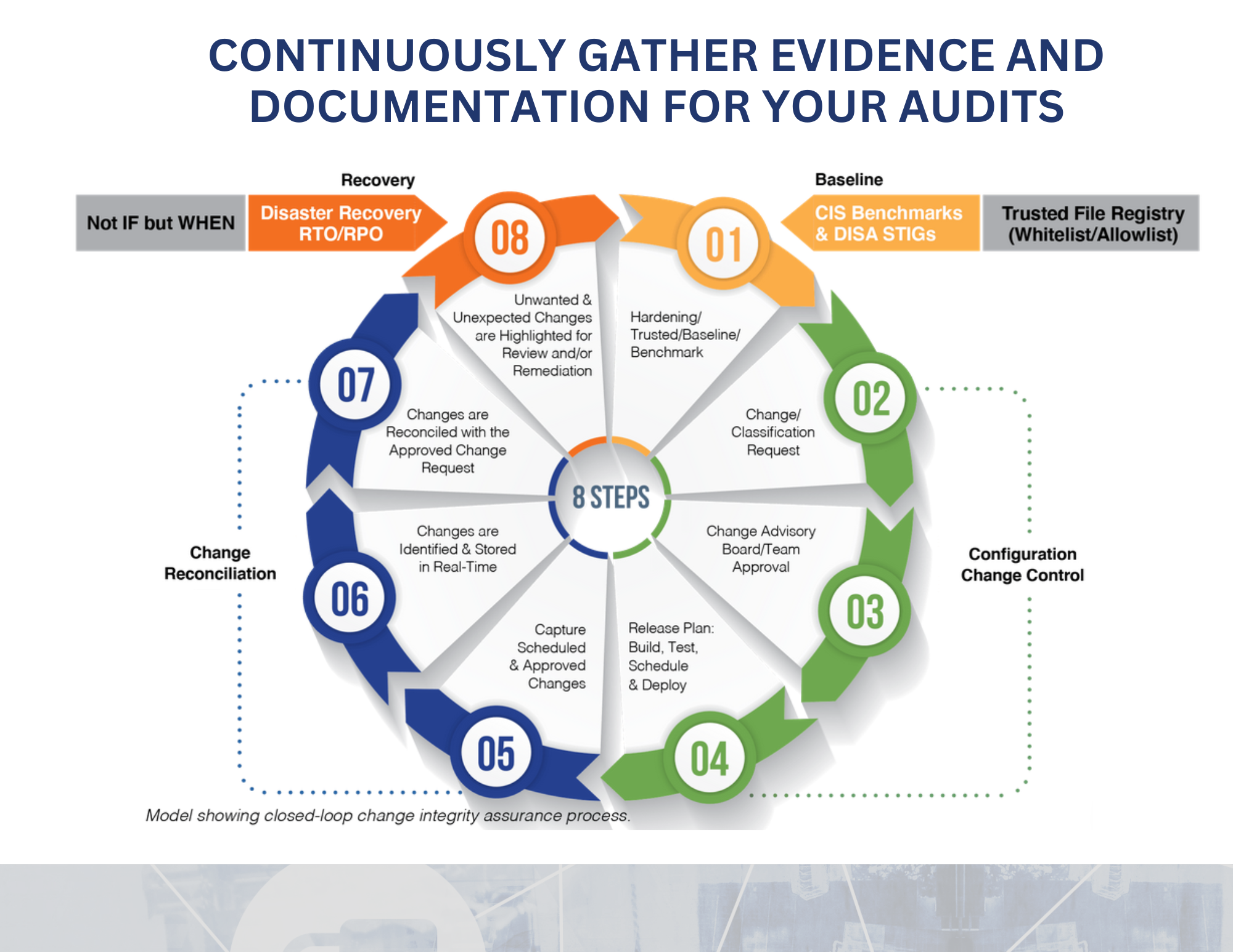
Organizations implement a File Integrity Monitoring solution for various reasons, like securing active directory and system files, data security, including zero-day attacks, and meeting the regulatory compliance standards or objectives with various regulations such as PCI-DSS, HIPAA, SOX, NERC, FFIEC, FISMA, GDPR, CMMC, CDM, SWIFT and more.
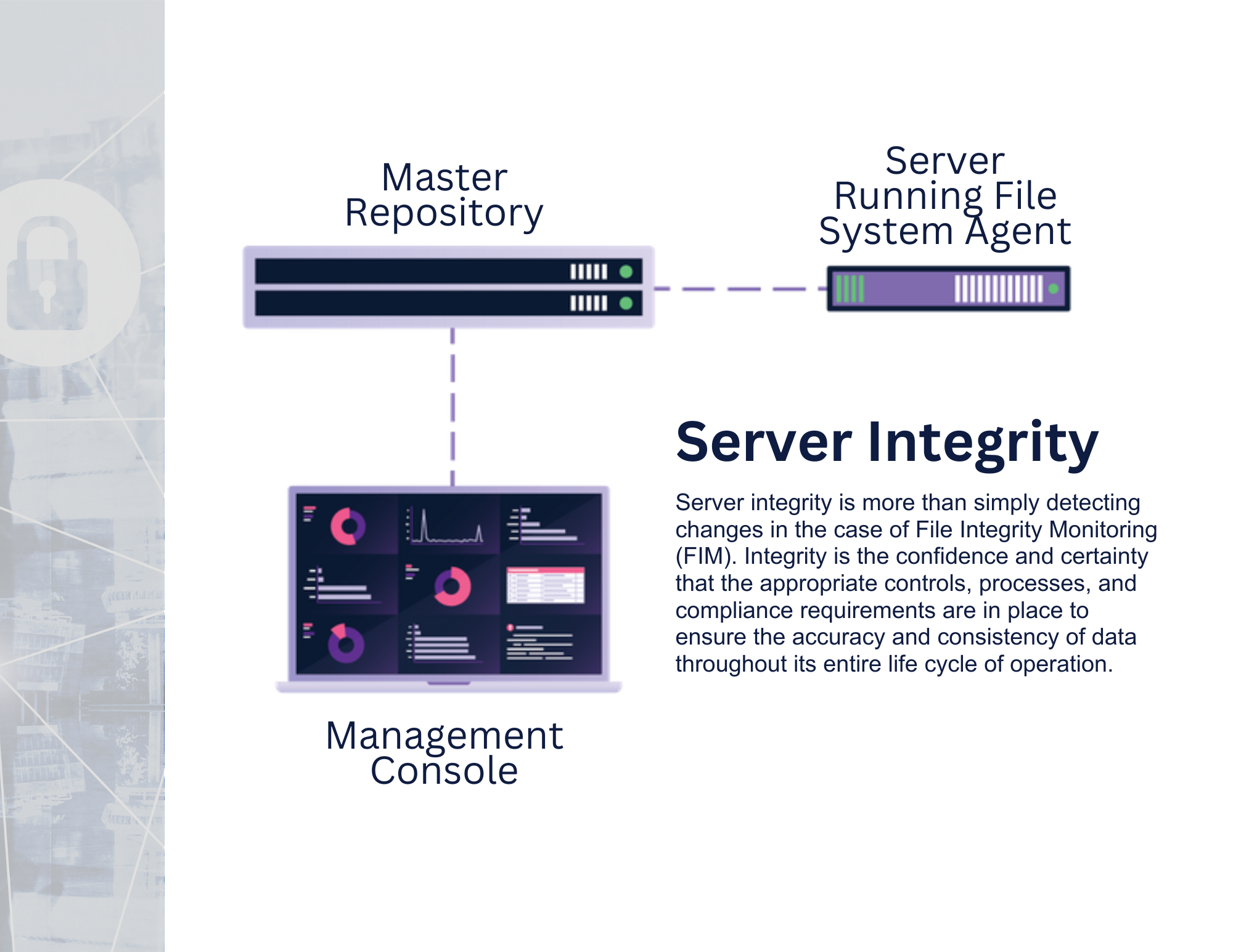
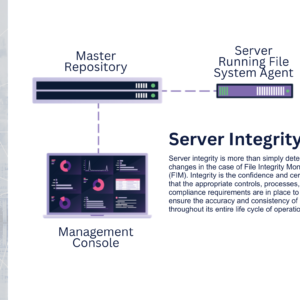
File integrity monitoring (FIM) is a crucial security practice that involves monitoring and analyzing changes to critical files on a system to detect and prevent unauthorized modifications or access. By regularly scanning and comparing the current state of files against their known, trusted baseline, FIM tools can quickly identify any unauthorized changes, such as tampering or malware infection, and alert security teams to take necessary actions.
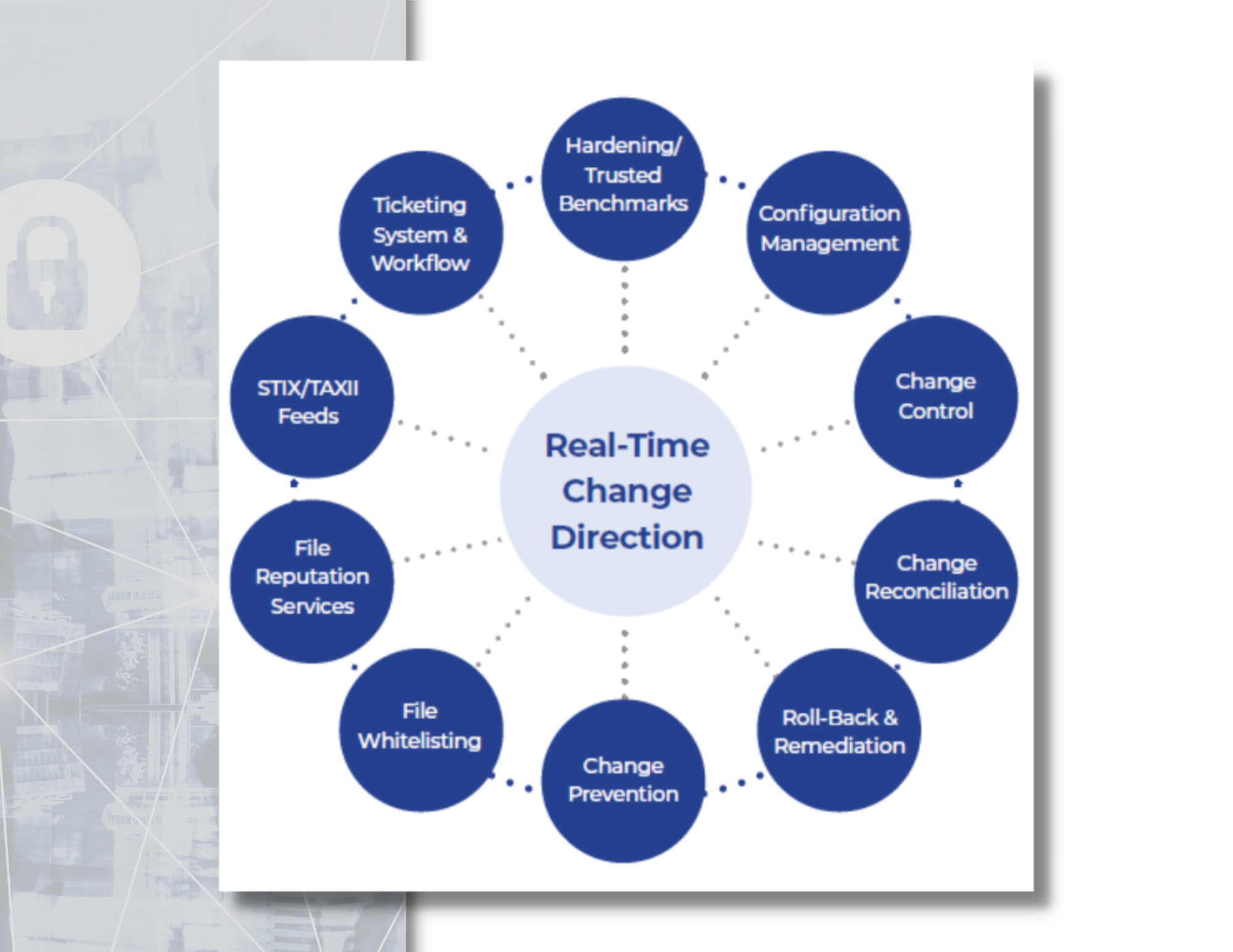
FIM can be implemented using a variety of techniques, such as checksums, digital signatures, or behavior-based analysis, and can be performed on both on-premises and cloud-based systems. Additionally, FIM can provide compliance benefits by helping organizations demonstrate adherence to regulatory requirements, such as PCI DSS and HIPAA.
Overall, effective FIM is a critical component of a comprehensive cybersecurity strategy, and organizations of all sizes should consider implementing FIM solutions to protect their valuable data and systems from unauthorized access and modification.