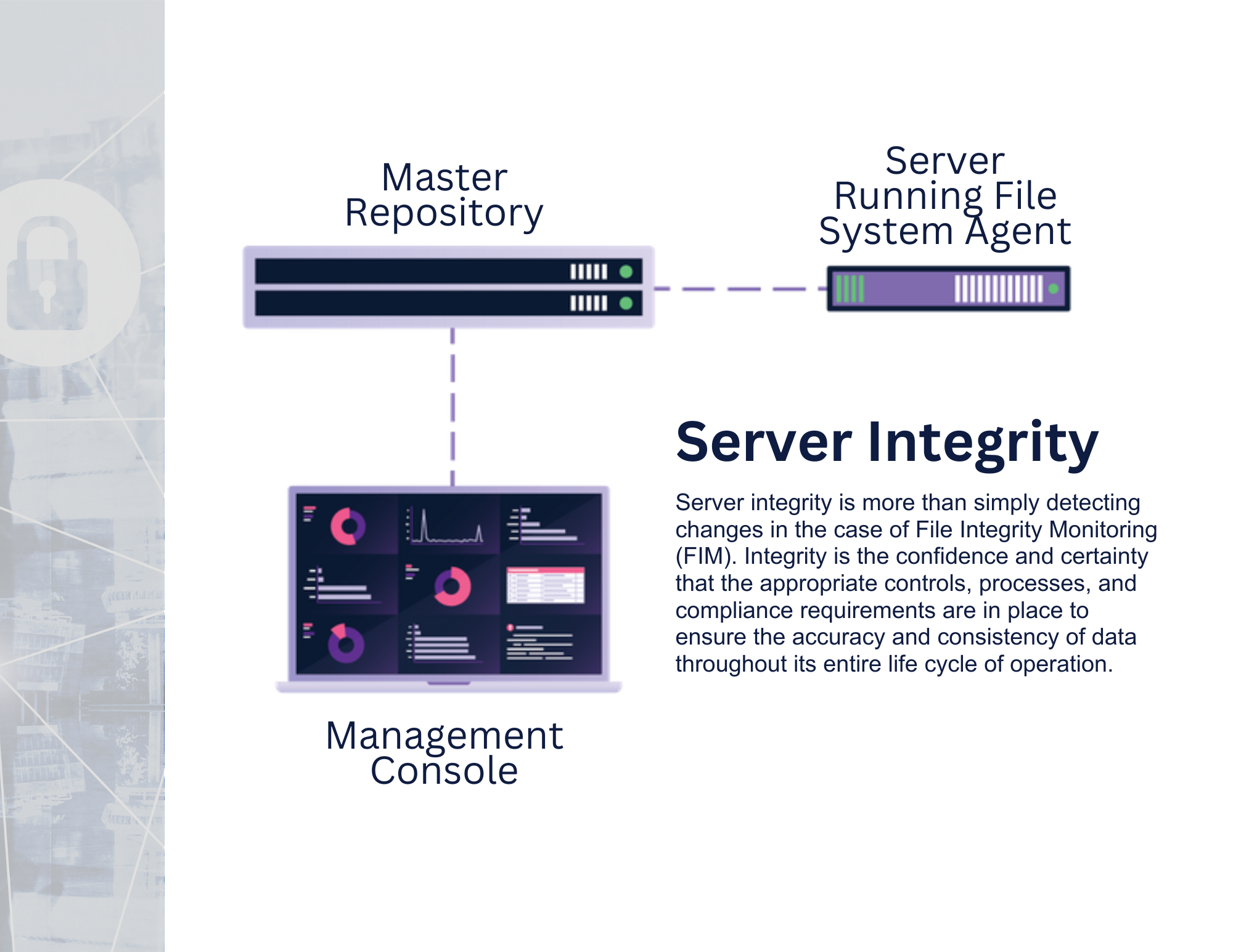
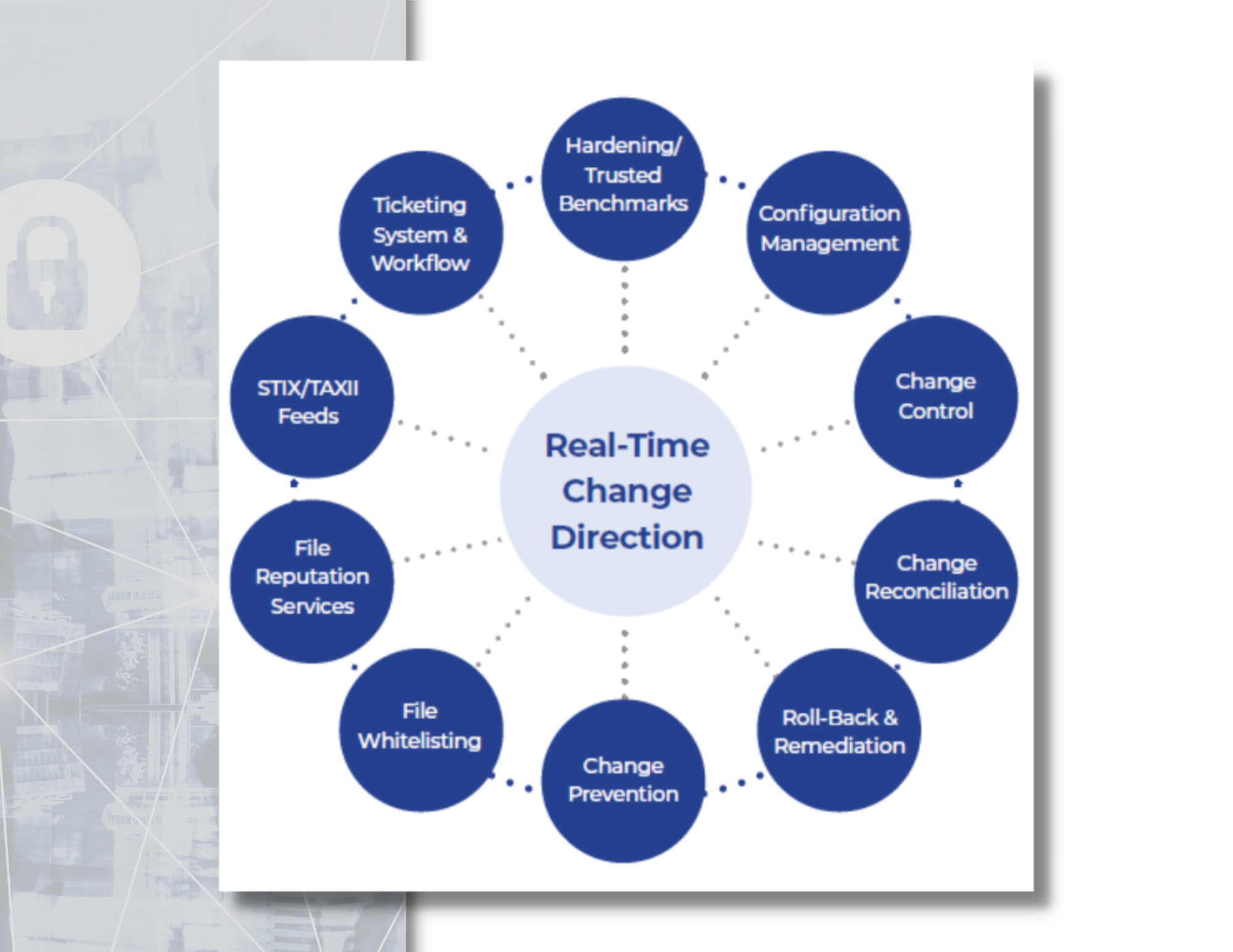
FIM provides the necessary controls and integrity assurance that your servers have not deviated from a known and trusted state of operation through best practices of system hardening, configuration, and change management. By managing the process of authorized and expected changes, server integrity can be maintained on an ongoing basis.
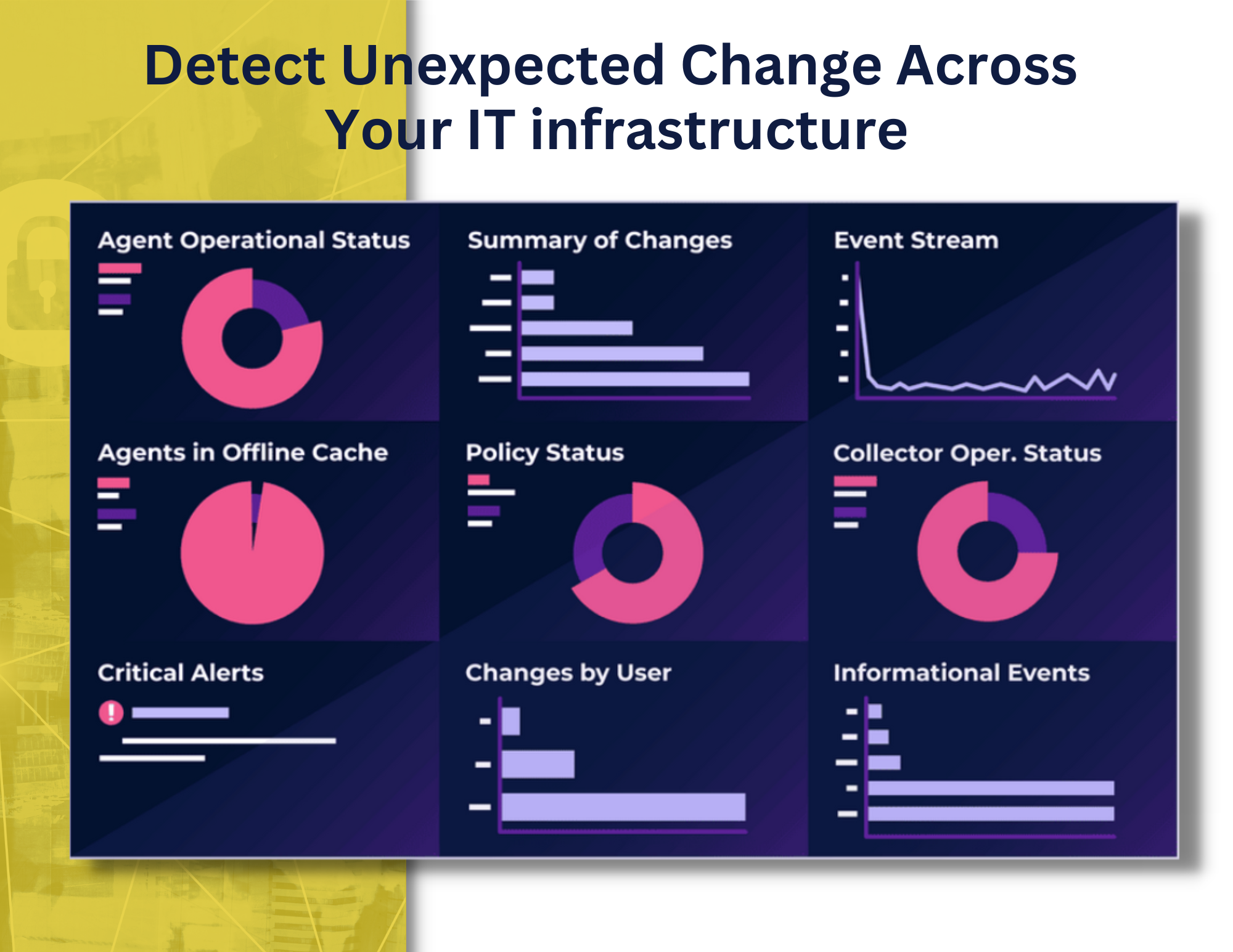
It all begins with the identification of change. This platform utilizes a patented real-time, proprietary methodology for detecting changes to servers. Once identified, it will interrogate that change with a number of best practice controls and processes to determine if the change is expected or unexpected (good or bad). The “expected” change will be suppressed and stored for audit and forensic purposes. The “unexpected” change will undergo further review and investigation to determine if it was a circumvented process (non-malicious) or a security incident (malicious).
In either event, a manual or automated process can be triggered to roll back and remediate to any number of previously trusted and secure baselines of operation.