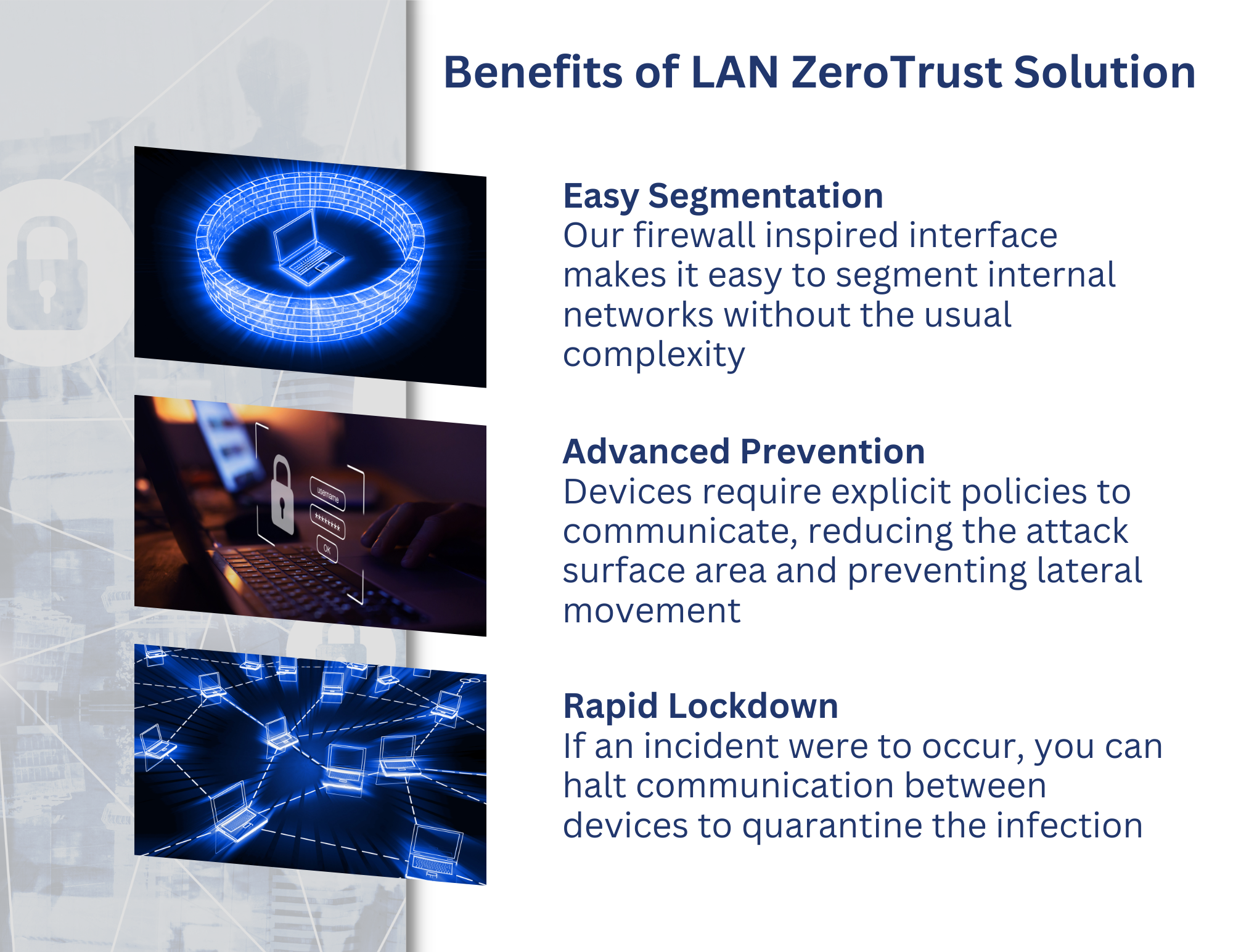
LAN ZeroTrust (LZT) is a unique technology to segment internal networks. Built with a firewall-inspired interface, controlling internal traffic has never been easier. It leverages a deny-by-default design where devices on internal networks can no longer freely communicate without explicit policies. LZT integrates with identity, empowering you to implement multi-factor authentication (MFA) policies where users must authenticate to access sensitive resources on the internal network.
- Segment Internal Networks: Easily segment internal networks without overhauling architectures, VLANs, or other complex solutions. Devices on the LAN are isolated, meaning they cannot freely communicate with each. Employees working from home, co-working spaces, hotels, coffee shops, and other shared networks are protected against local network threats as LZT prevents communication, making these devices essentially invisible. LZT policies also leverage multi-factor authentication (MFA) capabilities, helping to meet compliance requirements. Combining MFA with Todyl’s LZT also empowers organizations to develop sophisticated configurations where a user needs to MFA before a device can access the LAN.
- Rapid Lockdown During a Cyber Incident: With LZT, organizations can rapidly lock down their entire LAN during a cyber incident. With the touch of a button, all communication ceases between devices on the LAN, preventing communication and lateral movement of threats.
- Conditional Access to Sensitive Resources: Enforce strong access controls by requiring users to MFA before accessing restricted and high value internal resources.