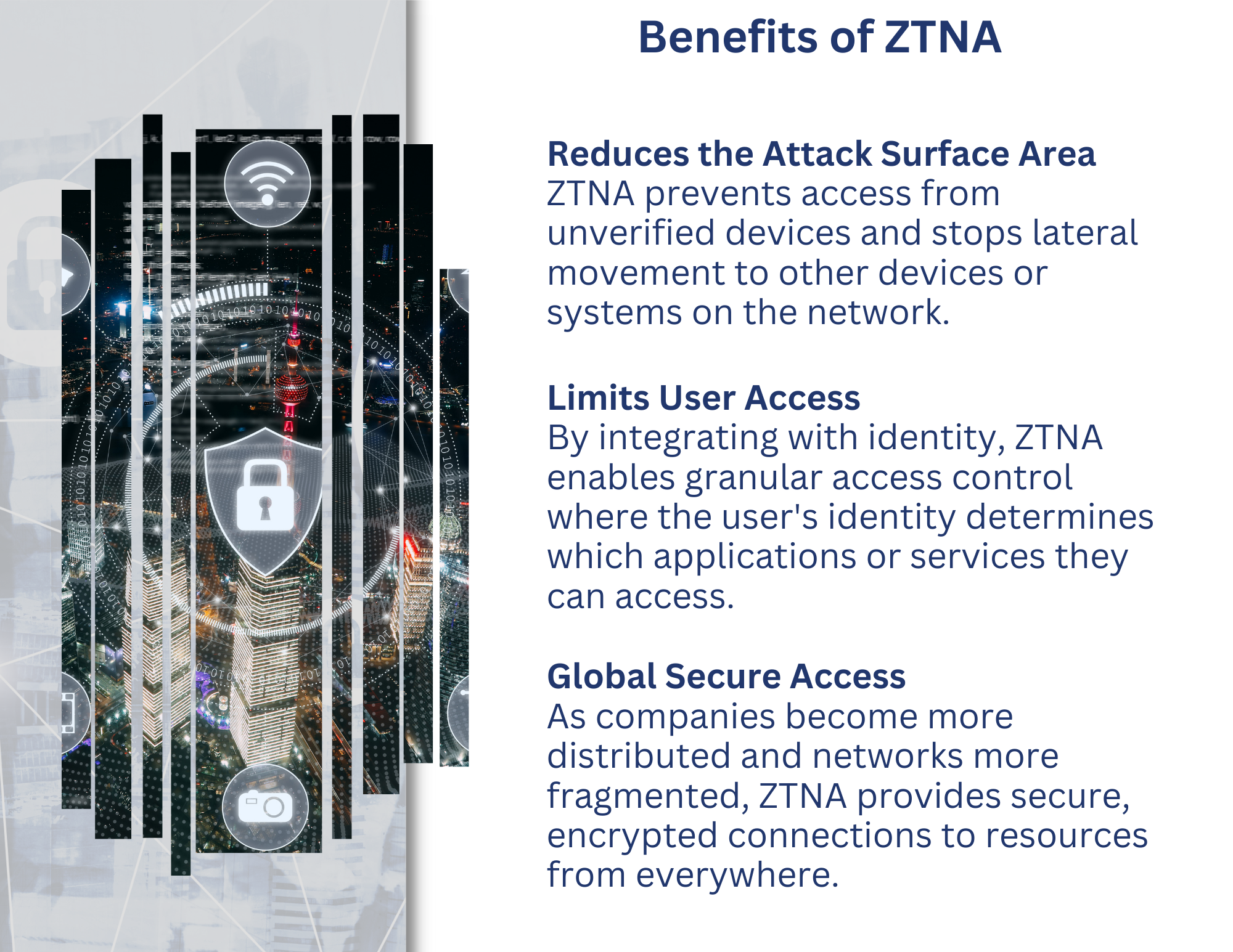
Zero Trust Network Access (ZTNA) provides granular, identity-based access control for secure remote access to applications and services. Zero Trust, as defined by Forrester, has four basic principles:
- Assume every network is hostile
- Create an invisible network to operate in
- Segment and isolate users and applications
- Deemphasize the physical network and perimeter, implement security everywhere
ZTNA eliminates implicit trust from networks, assumes every connection starts from an unknown and potentially hostile device, segments employees, and limits access to only the data and systems that employees need to do their job.
The SGN leverages a deny-by-default design and integrates with identity to allow a user to only access specific applications or services. It easily integrates with AzureAD, Google Workspace, Duo, and more. Organizations can create access policies based on user, device, MFA, and more to take back control in a distributed world. ZTNA prevents access from unverified devices and prevents lateral movement to other devices or systems on the network. There are several different use cases with ZTNA, including:
- VPN Alternative: VPNs are notoriously slow, easy for threat actors to circumvent, and challenging to manage.
- Securing Access to Resources: As companies become more distributed and networks become more fragmented, ZTNA delivers granular access control at scale.
- Mitigating Third-Party Risk: Contractors and other third parties often have more access to systems than they should, leading to significant security risks. ZTNA’s deny by default prevents unauthorized access.
ZTNA is a key component of the SASE module. SASE is the convergence of networking and security that supports the dynamic access needs for the work from everywhere world. In essence, it is the unification of several different networking and security technologies into a single platform. It connects and protects all your resources, whether in-office, on-prem, in the cloud, or mobile, making them securely accessible everywhere.
SASE enables fast, secure, and reliable connections to all your data, devices, networks, cloud environments, SaaS apps, and the Internet from everywhere. Our platform was built from the ground up based on Zero Trust Principles, unifying multiple powerful security and networking products. This integrated platform eliminates the cost, complexity, and blind spots from stitching together dozens of point solutions.