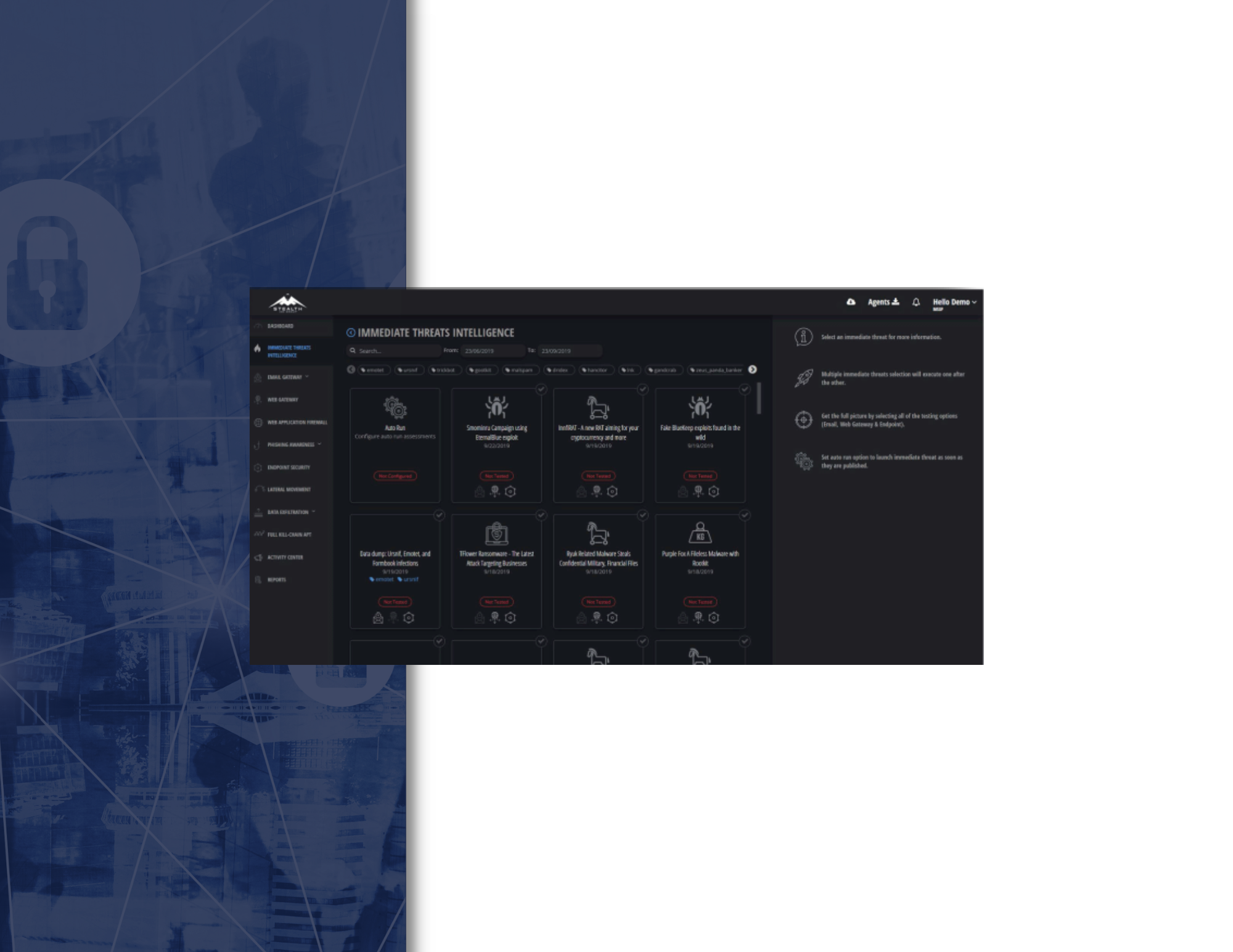
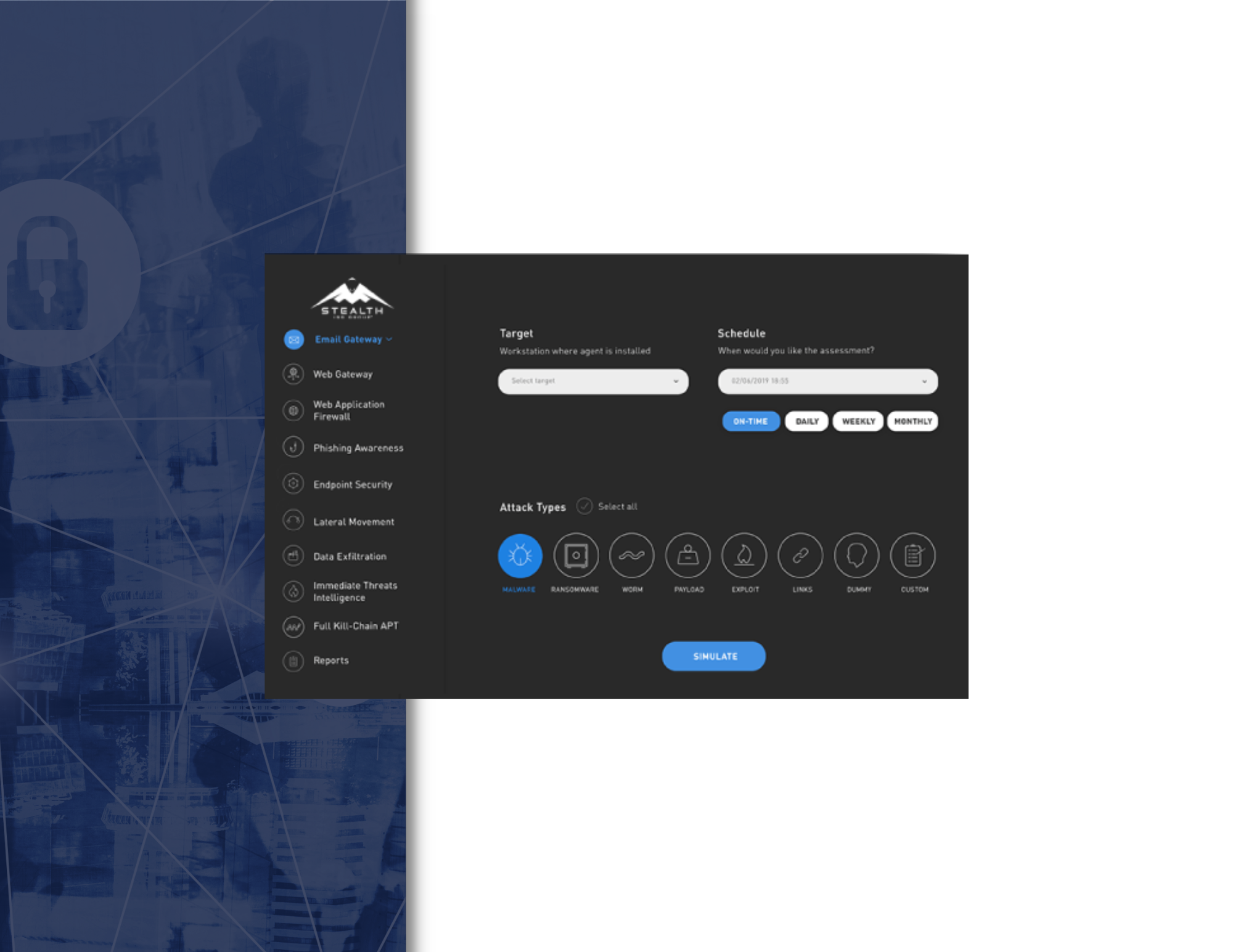
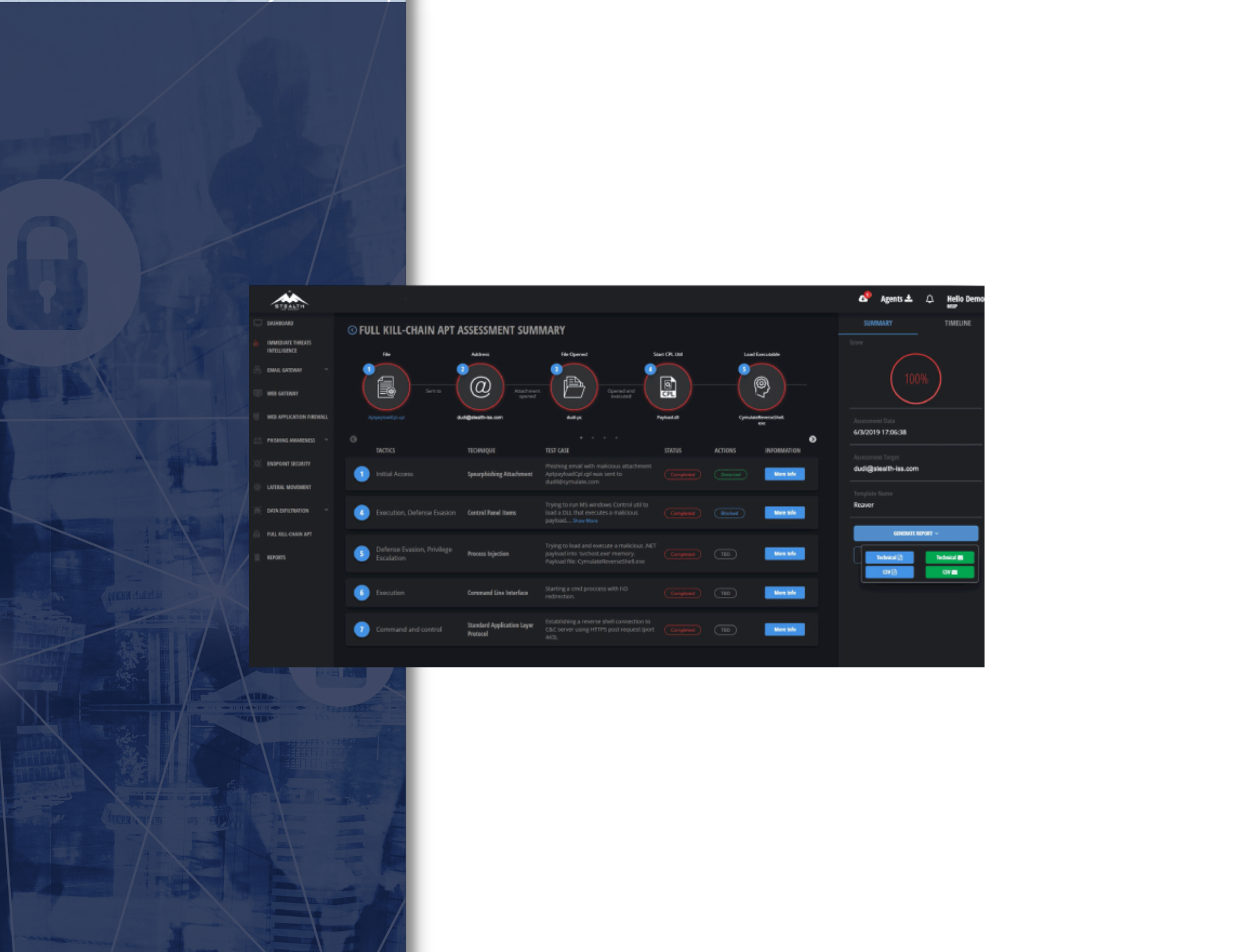
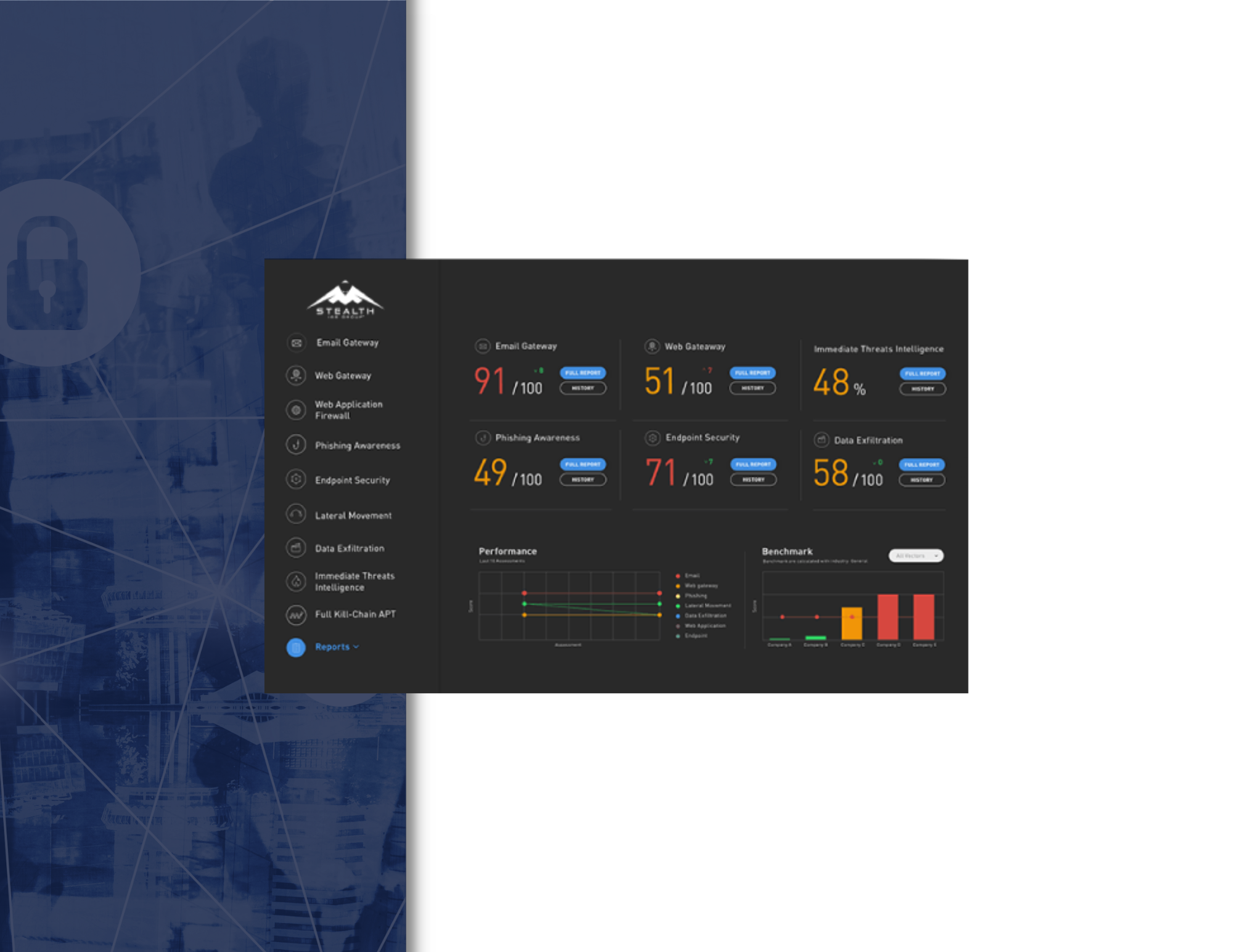
With the Web Application Firewall (WAF) attack simulation, we check if your WAF configuration, implementation and features are able to block payloads before they get anywhere near your web applications. We simulate an attacker who tries to bypass your organization’s WAF and reaches the web application, after which they attempt to perform malicious actions such as mining sensitive information, inflicting damage and forwarding users to infected websites using applicative attacks such as cross-site scripting (XSS), SQL and command injections.
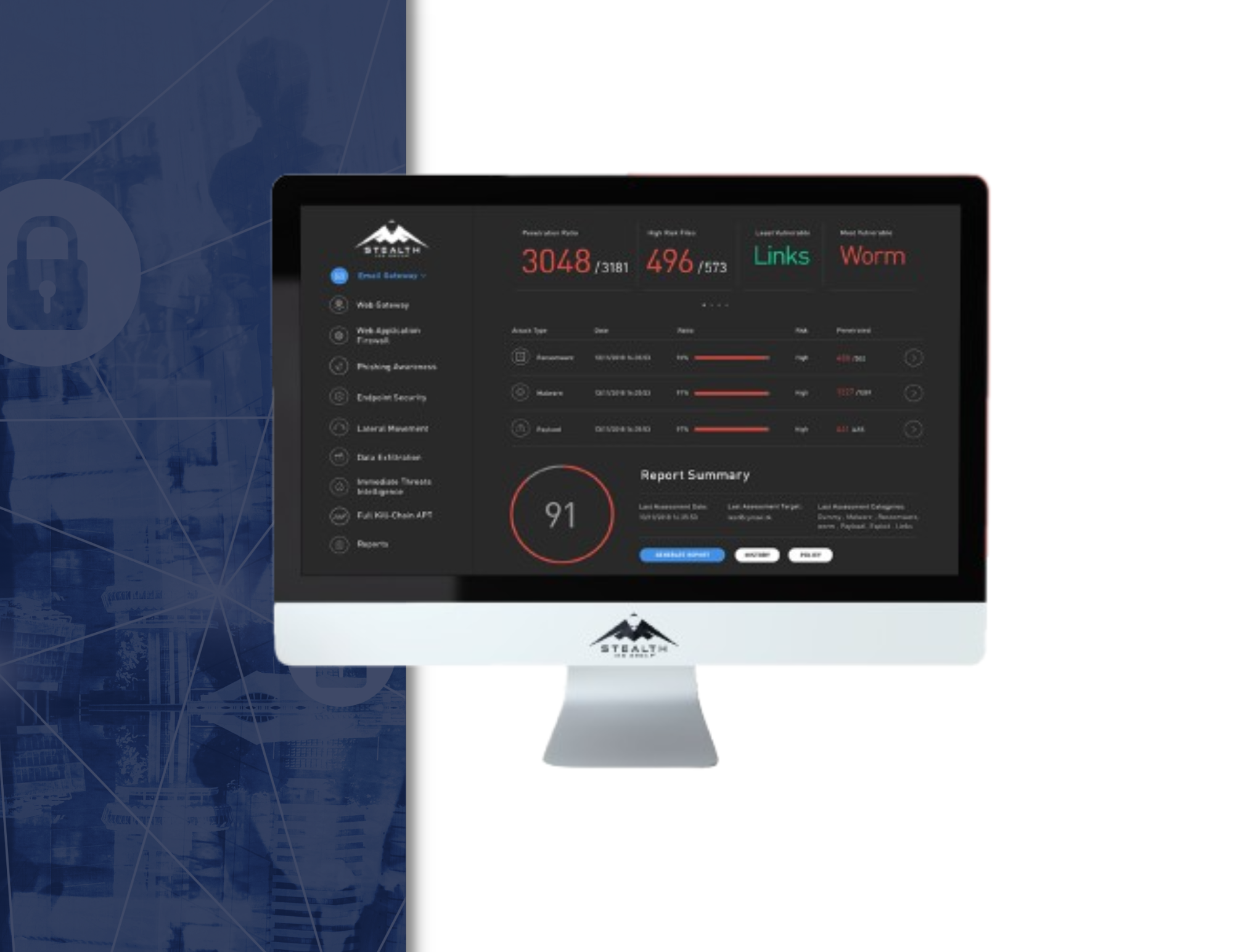
At the end of each WAF attack simulation, or other simulation vector, a Risk Score is provided, indicating the organization’s exposure, along with other KPI metrics and actionable guidelines to fine-tune controls and close security gaps.