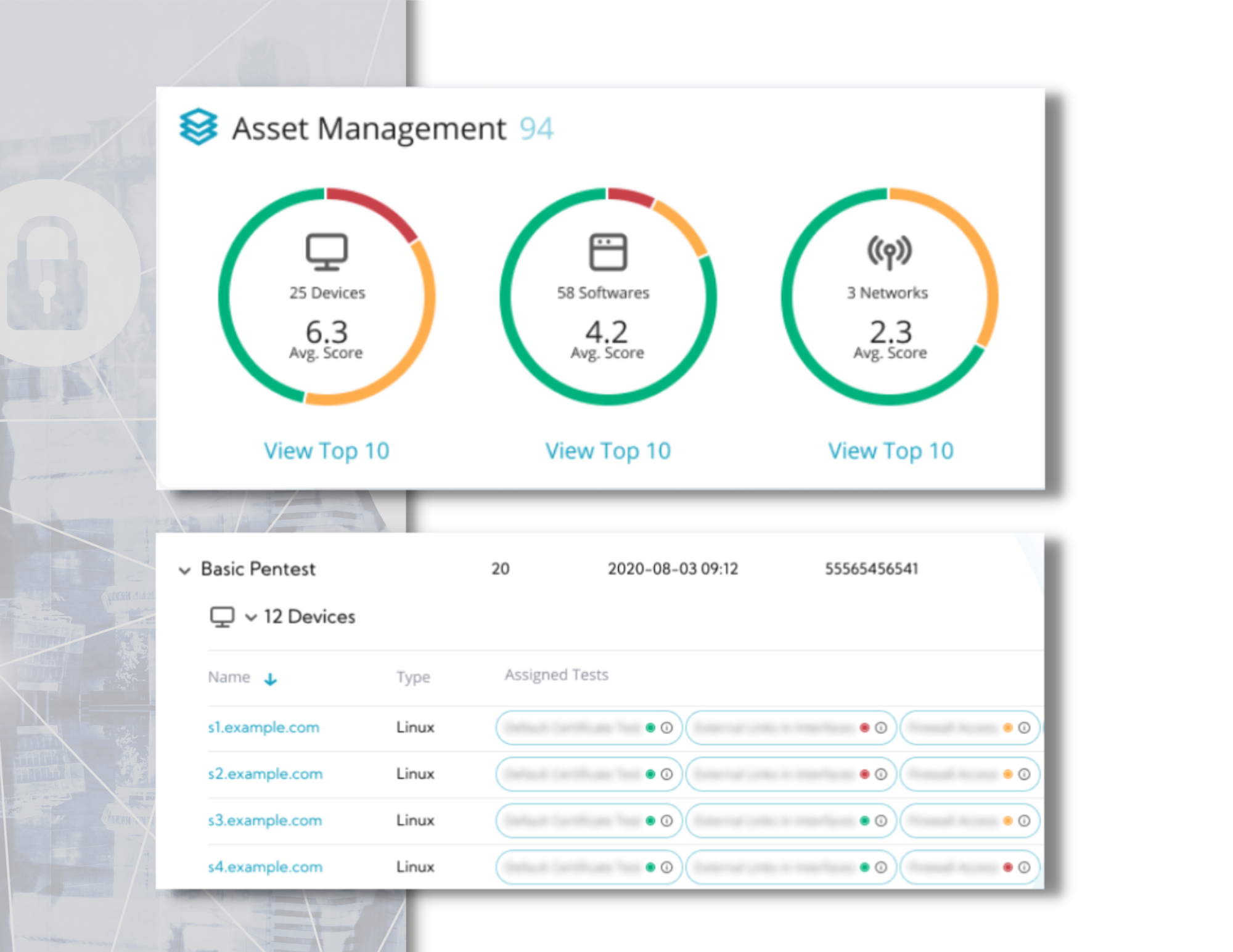
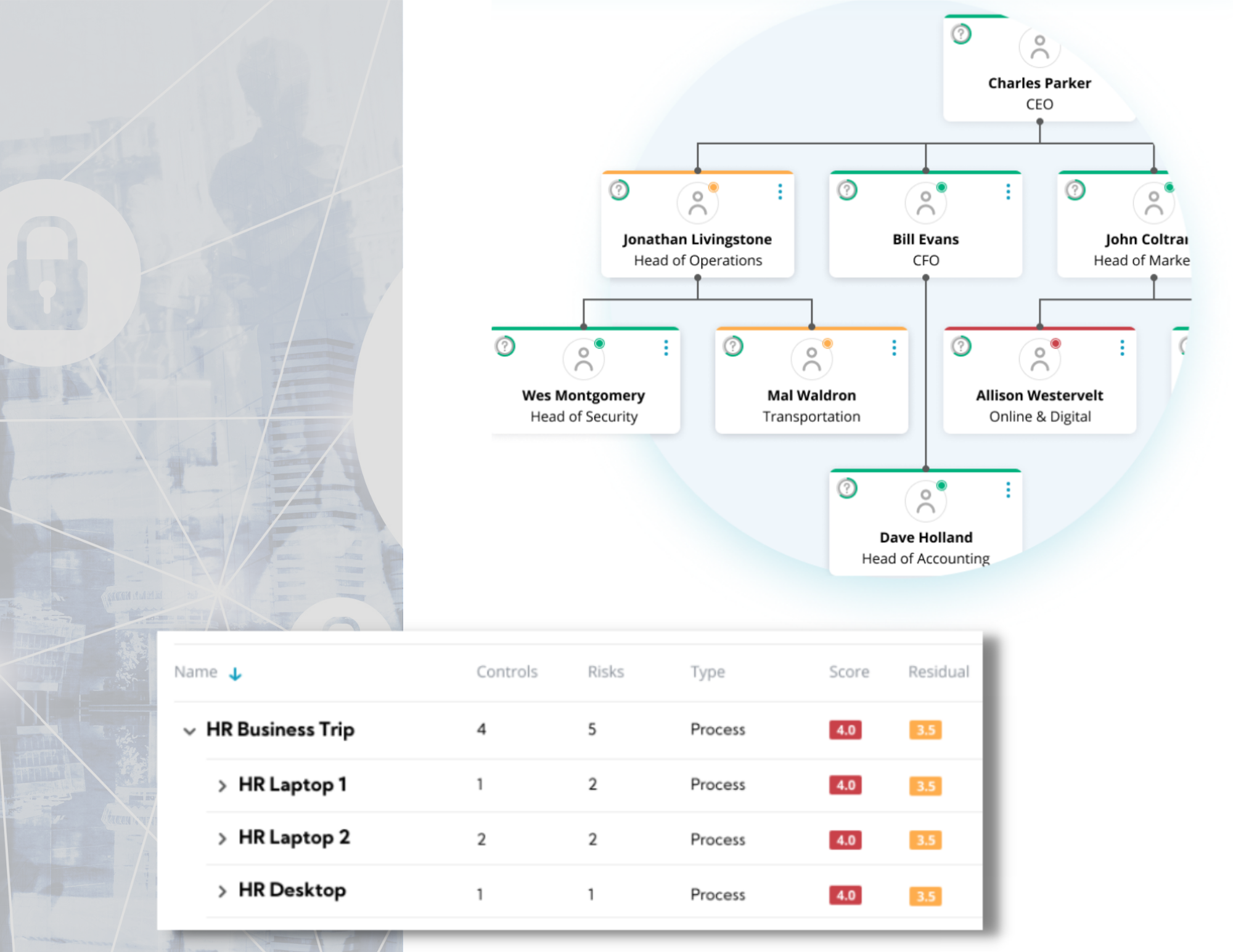
Moreover, small & medium businesses are struggling to keep up with ever stricter data-security standards. Before we came, SMB’s had to purchase multiple solutions, allocate resources, and integrate incompatible platforms in order to reach full security & compliance.
Compliance-as-a-Service provides end-to-end data security & compliance solutions allowing small businesses of every size to reach and maintain full compliance. This technology sets a new standard in security, comprehensiveness, integration, and affordability.
Reduce Risks, Reduce Complexity, Save Money
Automatically compliance and maintaining with our wizard – privacy and security measures according to the EU data-security regulations (GDPR), international data-security standards (ISO 27001) and other data-related regulations and standards.