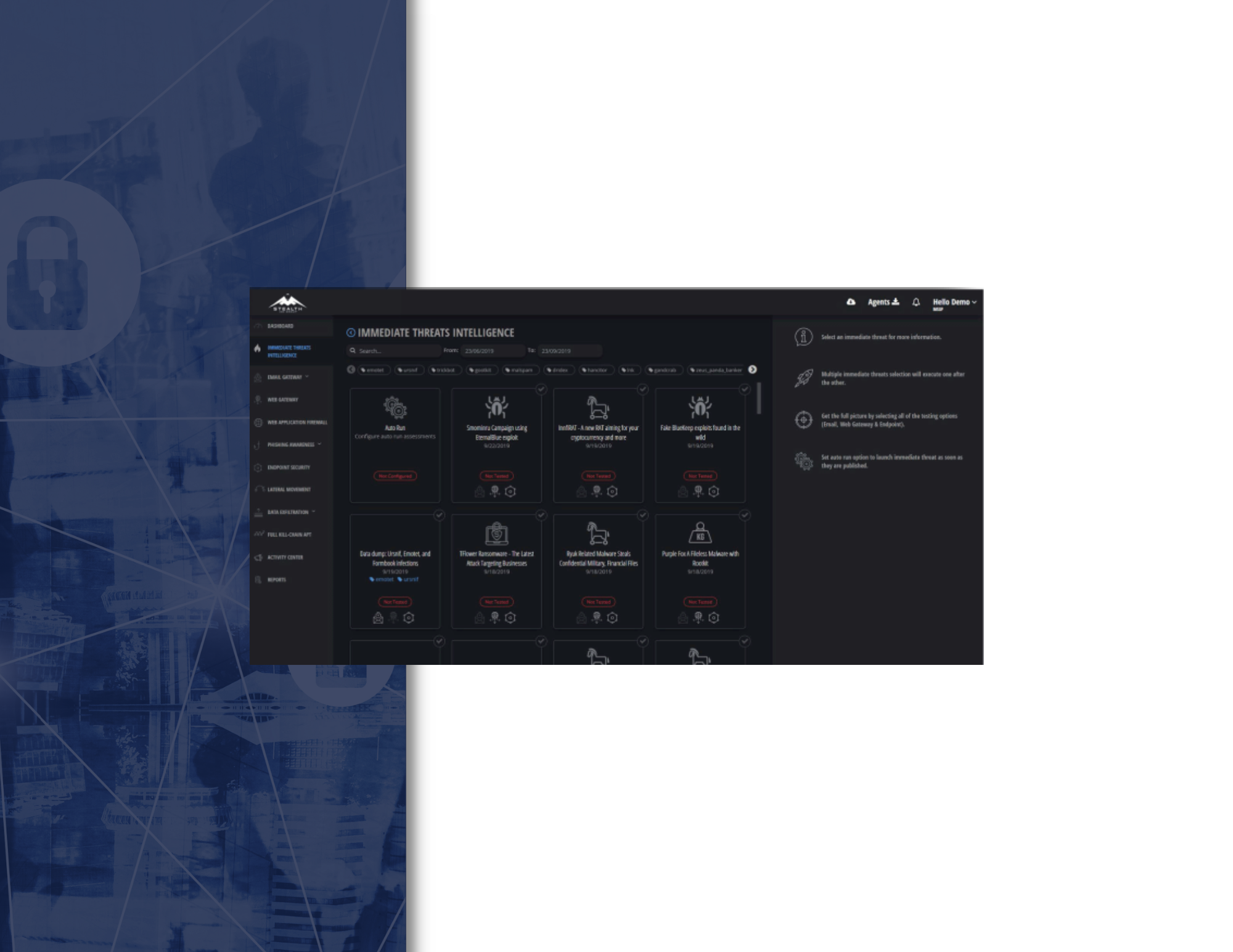
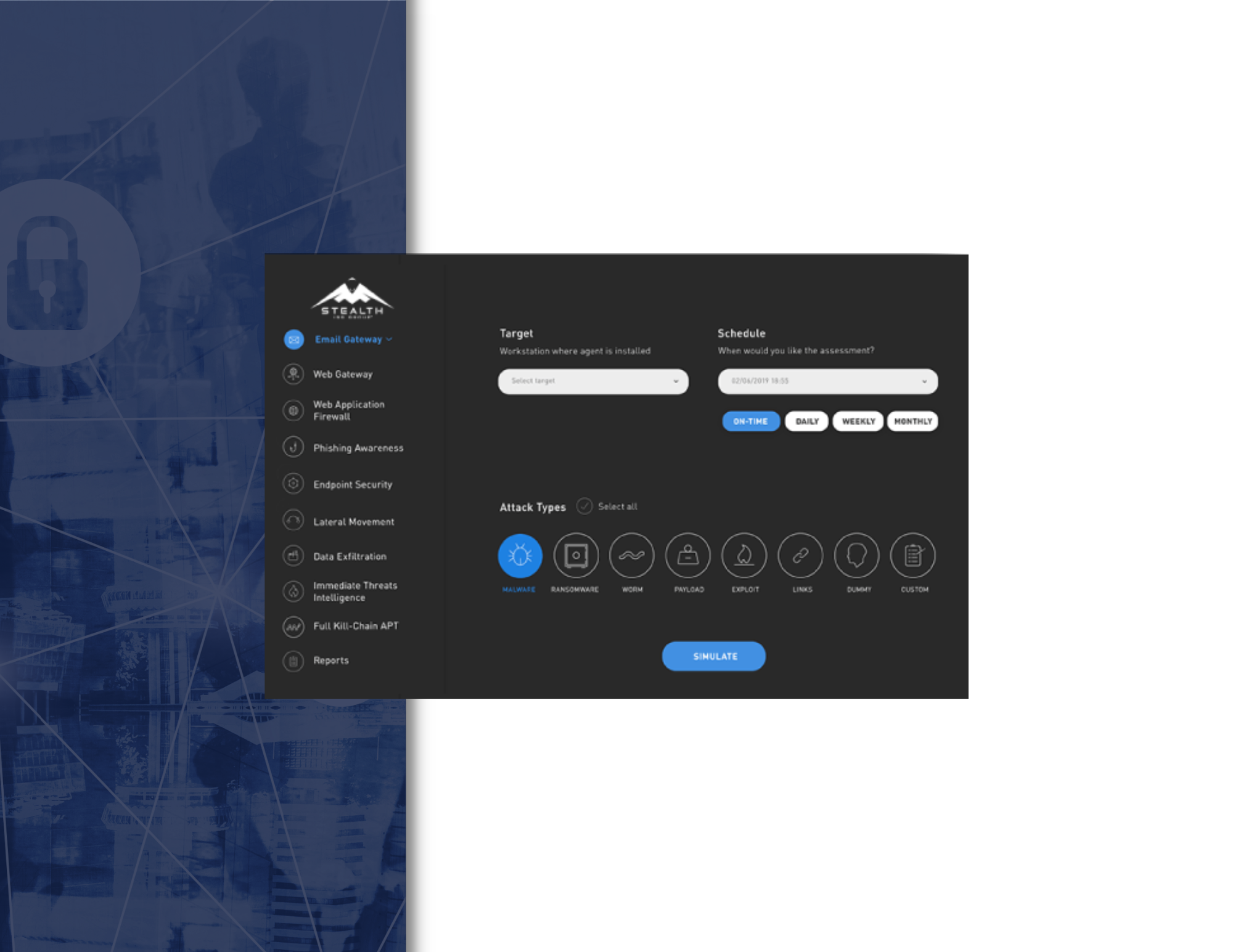
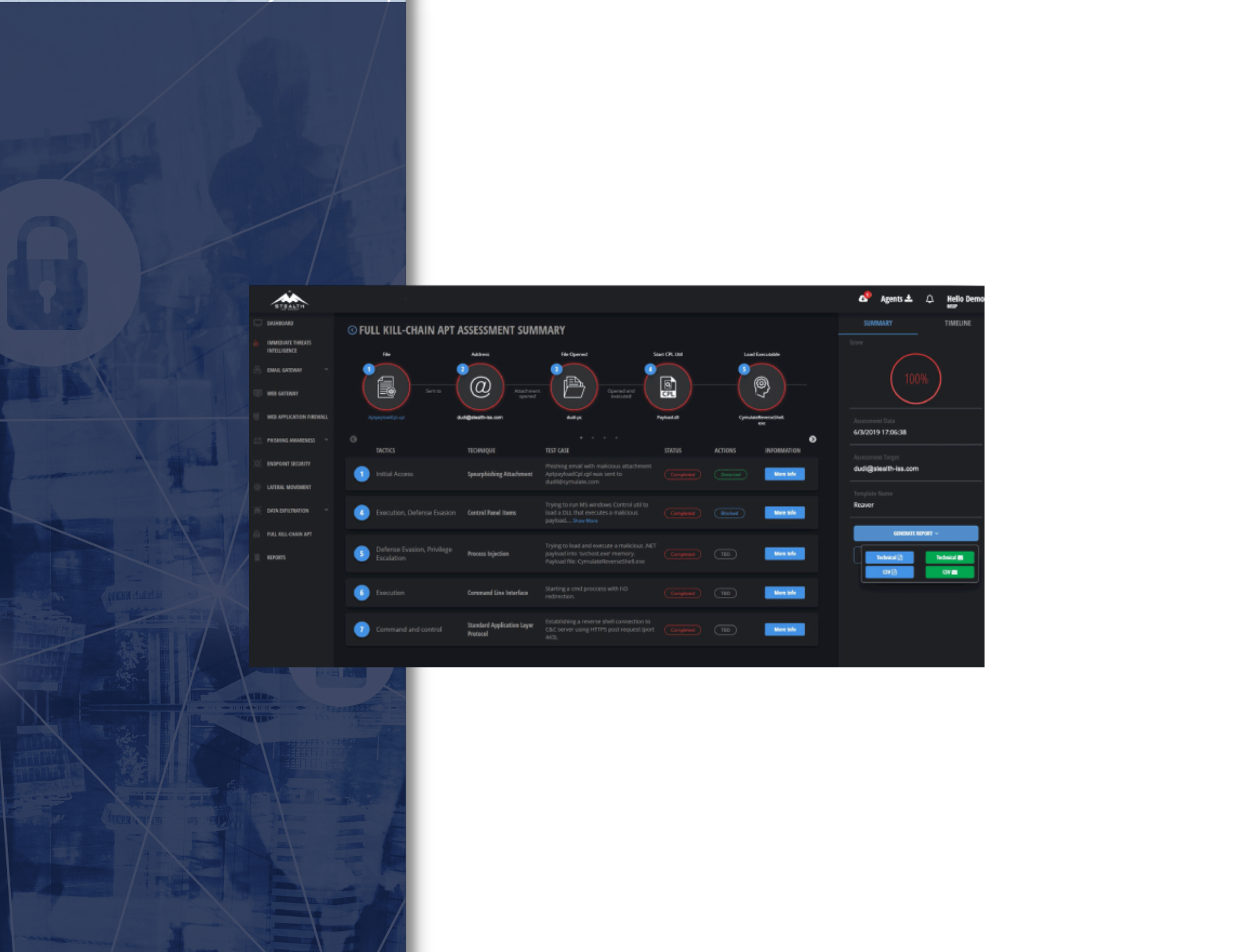
Manual methodologies to penetrate organizations and simulate hacker breach spots are limited in speed, volume and scope. The Lateral Movement simulated attack simulates a compromised workstation inside the organization and exposes the risk posed by a potential cyberattack or threat. Various techniques and methods are used to laterally move inside the network.
The platform uses a sophisticated and effective algorithm to mimic all the common and clever techniques that the most skilled hackers use to move around inside the network.
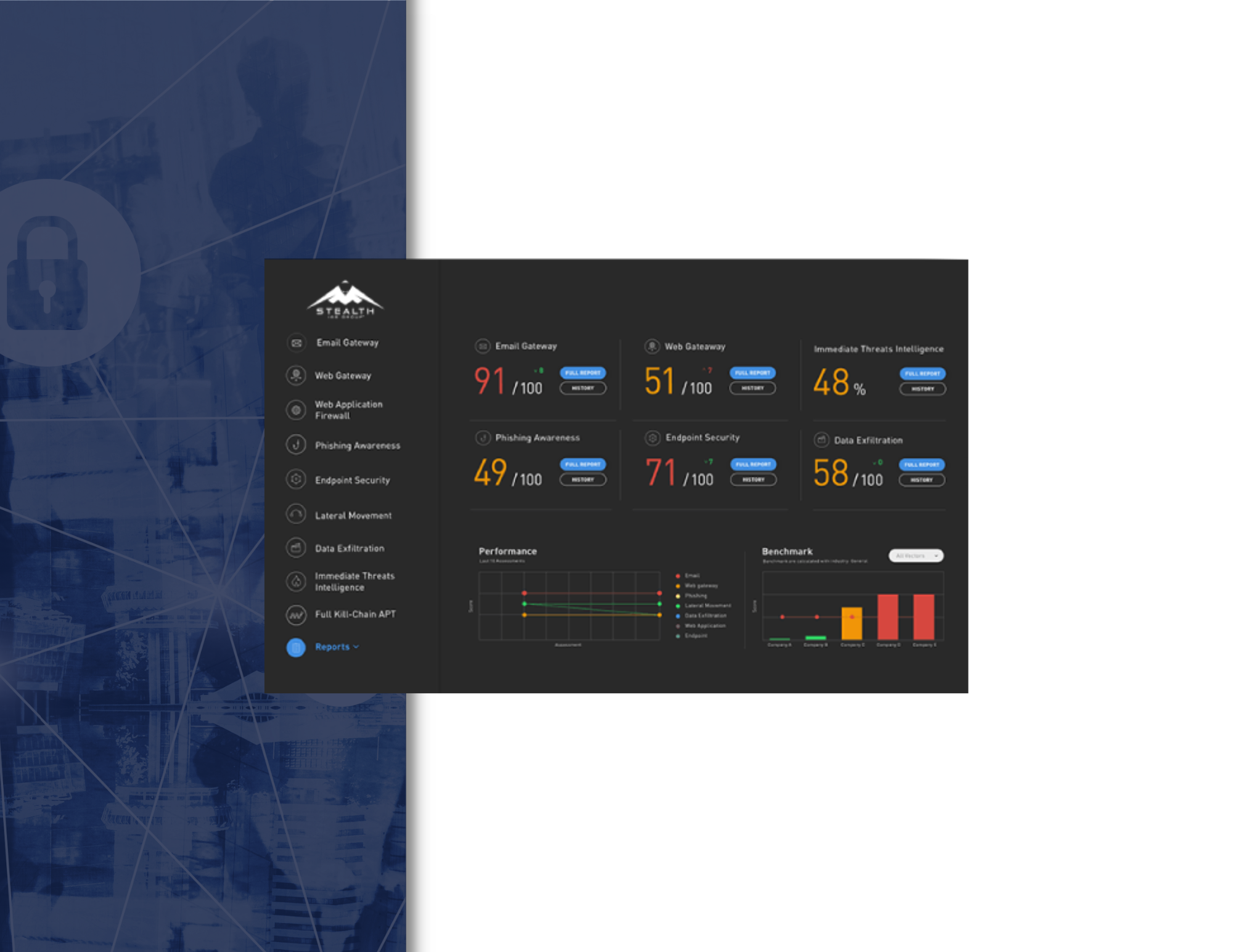
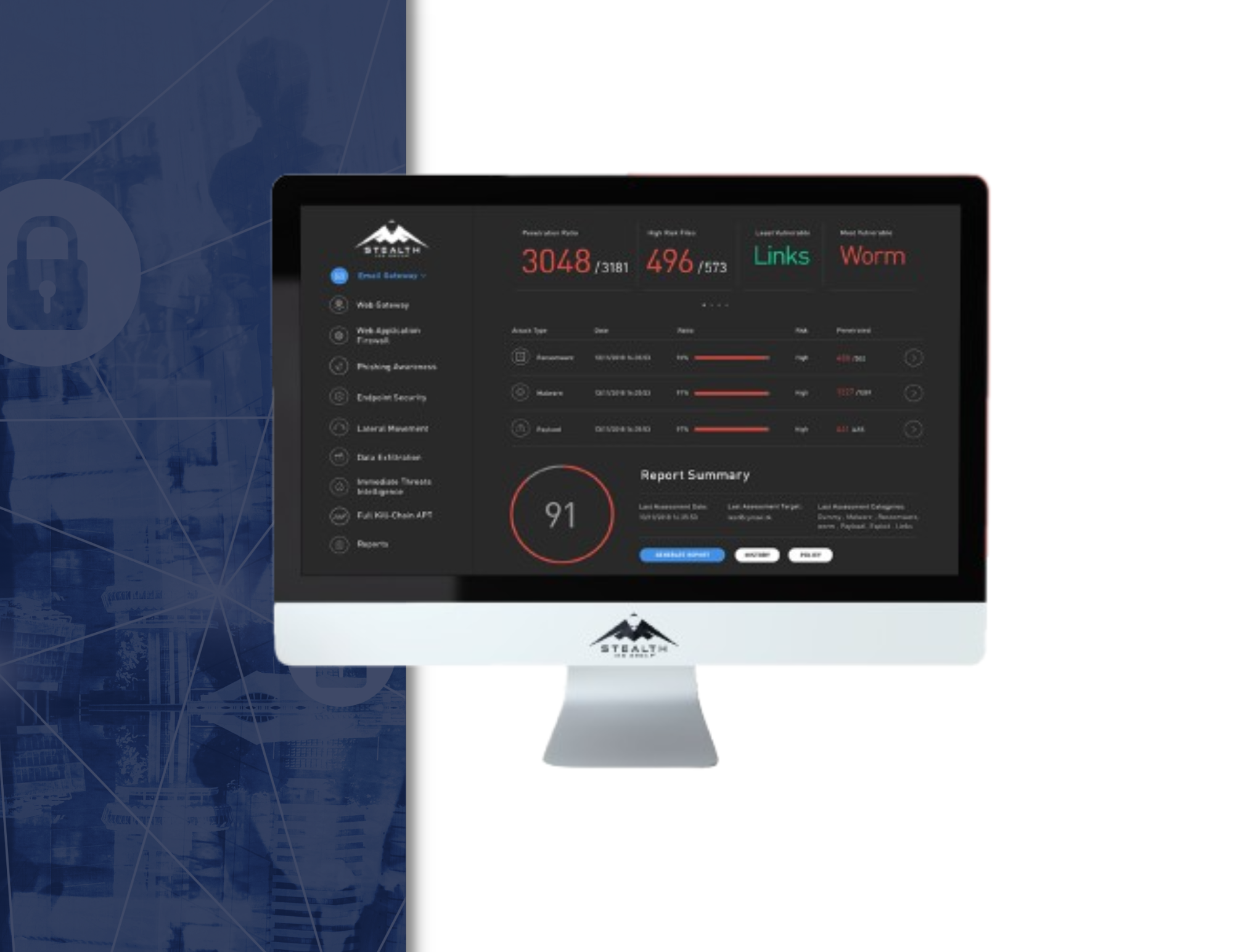
The Lateral Movement attack simulation results are presented in an interactive graphic diagram that shows the attacker’s lateral movement path, along with risk score, KPI metrics and actionable mitigation recommendations. By taking corrective action, IT and security teams can take the appropriate countermeasures to increase their internal network security.