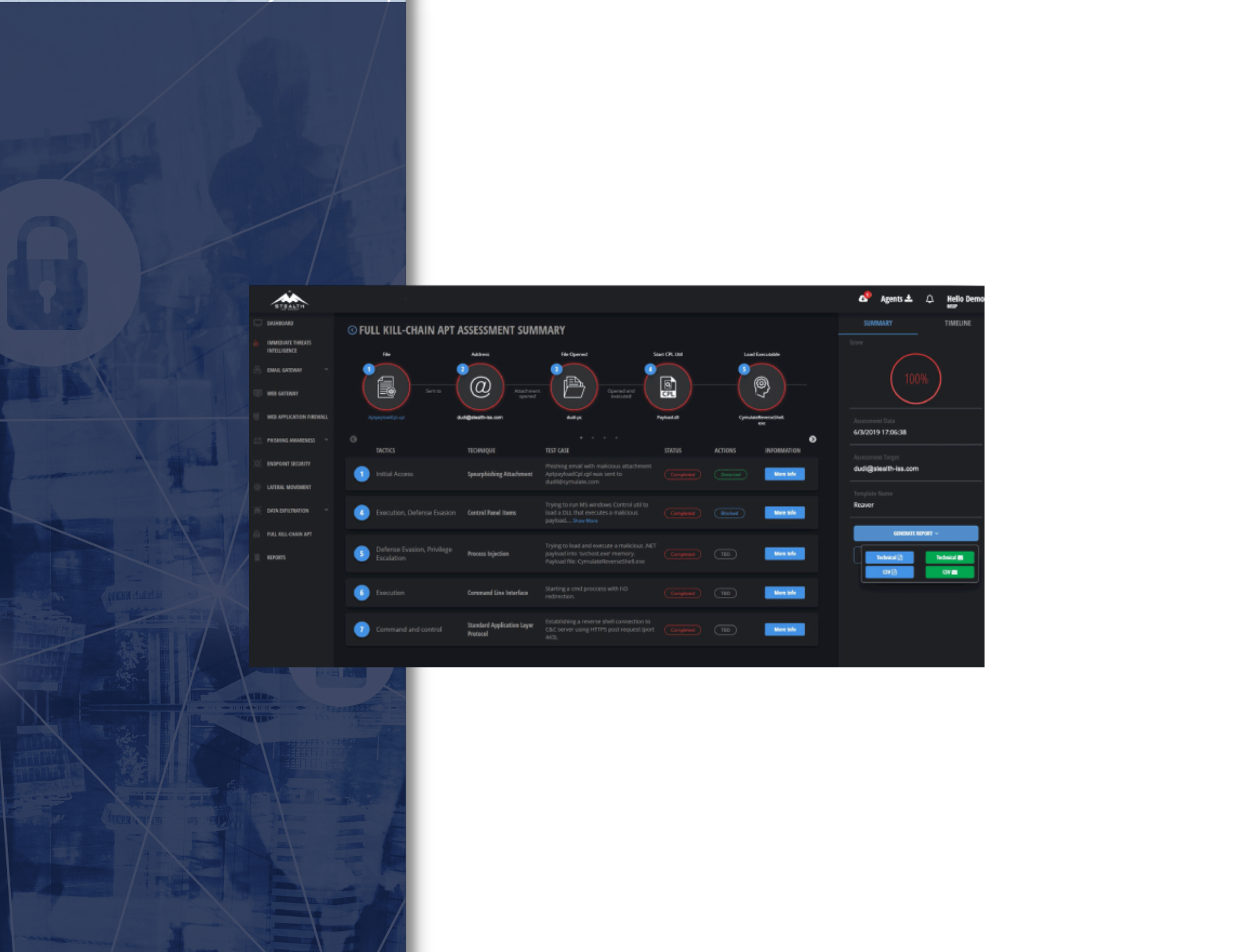
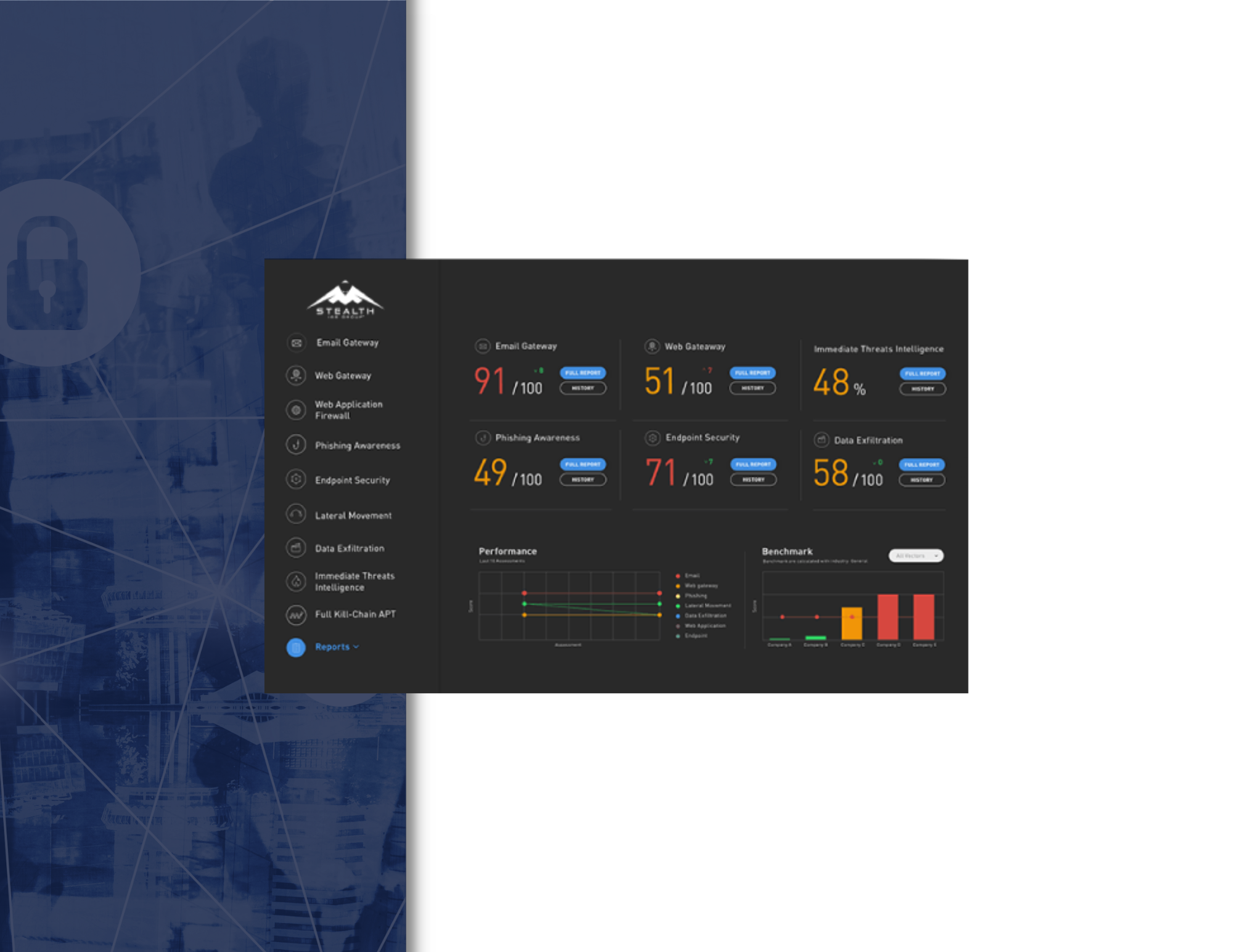
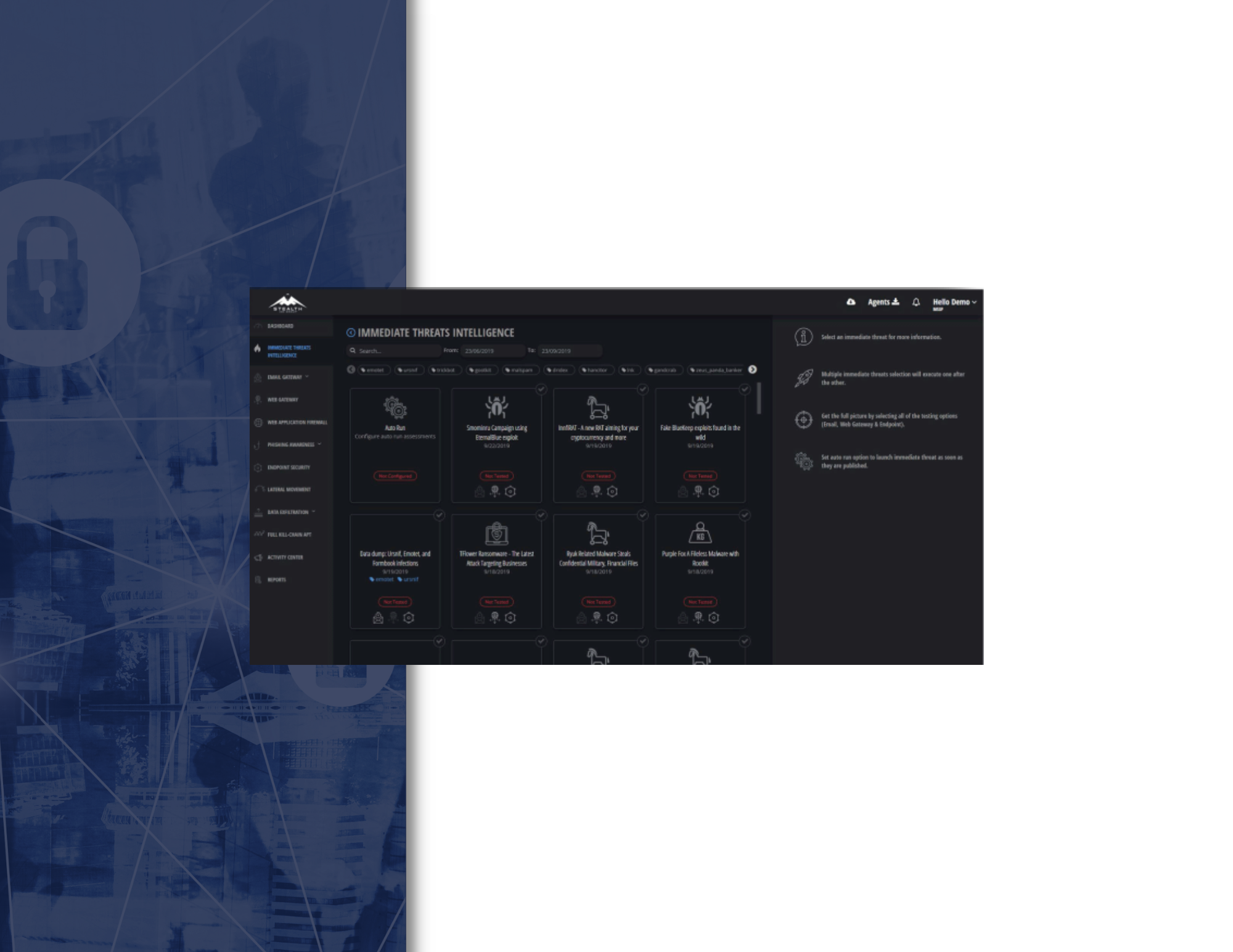
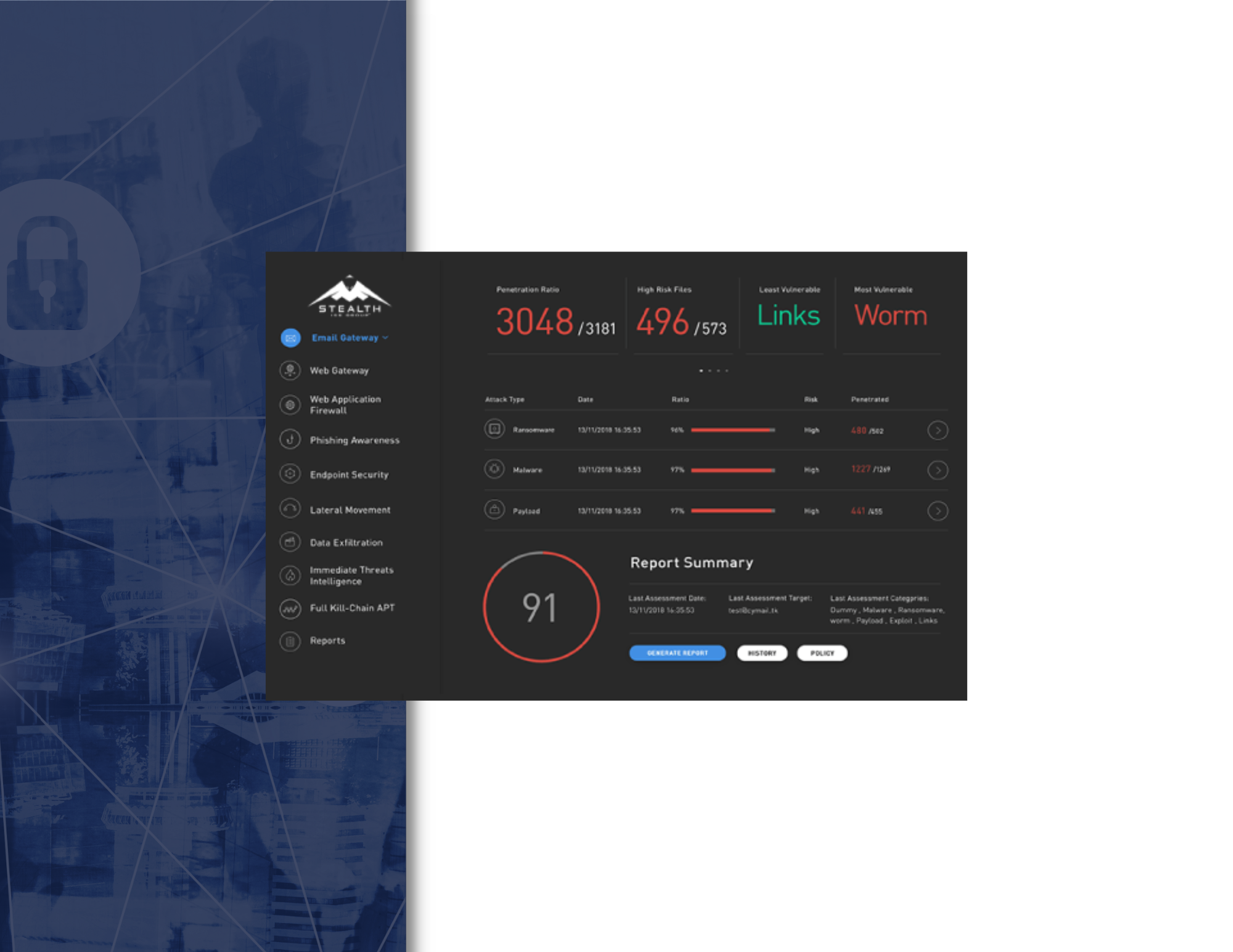
Testing Controls Across the Full Kill Chain
Since an Advanced Persistent Threat (APT) attempts to bypass security controls across the cyber kill chain, from attack delivery to exploitation and post-exploitation, defending against an APT requires testing the effectiveness of multiple security controls within your arsenal. Since the efficacy of one control affects the exposure of the next control in the kill chain, ascertaining if your defenses work against a full-blown attack becomes a daunting proposition.
Instrumenting your Security with APT Simulations
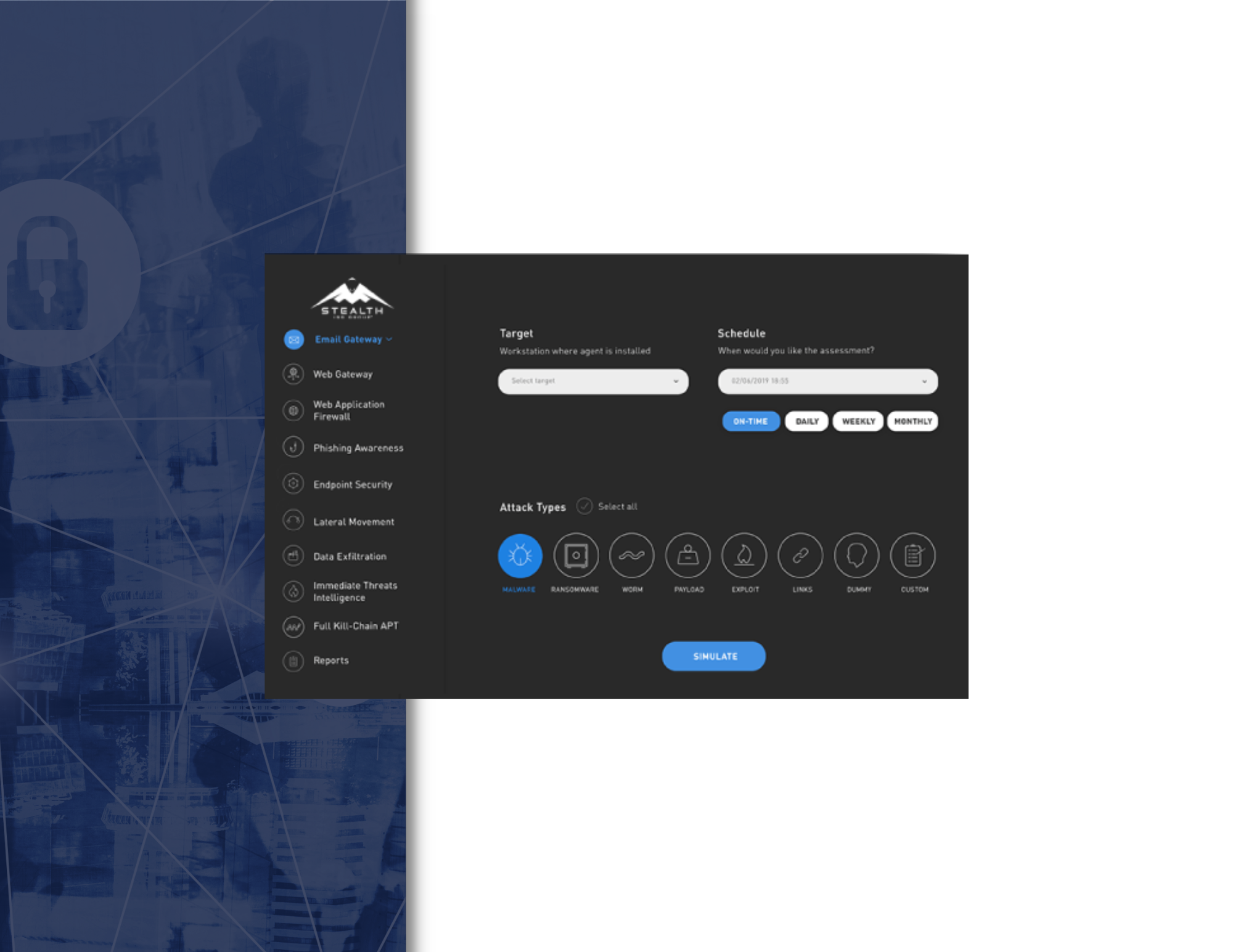
Our Full Kill-Chain APT Simulation Module solves the challenge of security effectiveness testing across the entire cyber kill chain by instrumenting your security framework in a comprehensive and easy-to-use manner. Instead of challenging each attack vector separately, organizations can now run a simulation of a full-scale APT attack with a click of a button, and gain a convenient, single-pane view of security gaps across their arsenal.
Simulated APT Attack Flow
As with a real APT, the different vectors are launched sequentially, one after the other, starting from a simulated attack on the email or web gateway, followed by endpoint security. Depending on the APT template chosen, the module may then challenge the organization’s network policies, to test for the ability to move laterally, and attempts to exfiltrate predefined sets of data, for example mock PII, mock medical records, payment details etc., testing the effectiveness of your DLP controls.
Actionable Insights and Reporting
An attack simulation is only as effective as the corrective steps taken to remediate identified gaps.
At the end of each APT simulation, the following actionable insights are automatically generated and delivered:
- The outcome of each attempted step of the APT attack is shown, e.g. Success, Failure or Partial Success.
- An exposure score that takes into account potential asset impact, infection success rate, and probability of encounter.
- Remediation and mitigation guidelines that map to the MITRE ATT&CK framework for additional context.
- KPI Metrics offer quantifiable security posture benchmarks, and an immediate, objective understanding of where you are most vulnerable so you can prioritize remediation efforts and resources. These metrics also provide a way to measure security controls performance over time, and compare yourself to others in your industry.
- Executive and Technical-level briefs summarize simulation results for the board, or detailed for your technical team so that it has the information it needs to reduce your attack surface.